ISOutsource Blog | Featured Article
No Results Found
The page you requested could not be found. Try refining your search, or use the navigation above to locate the post.
Leading with empathy: How to achieve the value in understanding each other
While KPIs and metrics might indicate that teams have made the transition successfully, it is important to not lose sight of the unprecedented levels of...
Helping businesses proactively anticipate change, innovate, transform, and realize their full potential
Corporate Culture, Security, Technology, Trends
The Covid-19 pandemic was a rude awakening to many small and medium businesses who viewed technology as a necessary evil and were entirely...
Helping Businesses Emerge Stronger From The Pandemic
Business, Corporate Culture, ISOutsource News, Managed Services, Outsourcing, Tech Education, Technology
However, visionary leaders who are optimistic by nature see those challenges as opportunities to innovate. The ISOutsource leadership team saw the...
The IT Vulnerability Management Tool Your Business Needs
Is your business protected from security vulnerabilities? Business technology can get complicated quickly. It’s become increasingly more difficult...
What is GRC and How Can it Help Your Business?
What is GRC? GRC is an acronym for Governance, Risk, and Compliance. It refers to a business or organization’s ability to synchronize its...
The Best IT Consultants Throughout The Pacific Northwest
Finding the best IT consultants in the Pacific Northwest isn't always easy. Businesses have to carefully consider services, pricing, availability,...
Do This To Add Value And Expertise To Your Organization
Adding value and expertise to an organization doesn't have to mean spending months sourcing the right IT talent. Instead, investing in onshore help desk...
The Role Expert SMEs Can Play In Improving ROI
Many businesses try numerous methods to improve their ROI, but one of the best approaches is using expert SMEs. Using these subject matter experts...
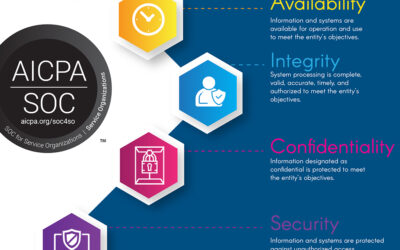
ISOutsource Attains SOC 2® — System Operations Controls for Service Organizations: Trust Services Criteria—Type 1 Attestation.
ISOutsource News, Press Release
ISOutsource Attains SOC 2® — System Operations Controls for Service Organizations: Trust Services Criteria—Type 1 Attestation. AICPA System and...
5 Of The Most Popular Services Businesses Outsource
IT outsourcing is becoming more popular as businesses seek to get more from their IT budgets. From getting specialized services for temporary projects to...
4 Impacts On Your Business Of Endpoint Security
Cybersecurity is a concern for every business, but the right endpoint security solution helps protect devices and data. It's more critical now than ever...
Customize Your Business With Amazon Web Services EC2
After working with numerous businesses and our own personal experience, we can say that there isn't a one-size-fits-all solution for IT. We often hear...
4 Ways Big Business Can Benefit From Wireless Infrastructure
Most businesses look up to big businesses to see how the latest tech trends affect growth. However, some of the biggest businesses still haven't fully...
The Best Email Security Solutions For 2019
Email is currently responsible for spreading 92% of malware. Even worse, one in 50 emails contains some form of malicious content. All it takes is a...
The Upside To Hyperconvergence
One of the biggest complaints we hear from businesses is the cost and effort necessary to scale their business. In many cases, we recommend...